The website bitcoin.com published a blog post on Saturday, February 3rd, titled Ledger Addresses Man in the Middle Attack That Threatens Millions of Hardware Wallets. Some of the claims made in this post are unfortunately incorrect.
This is not a Ledger security flaw. Ledger users are not at risk, as long as they verify their new receive address on their device when they share it to receive fund. As far as we know, no user has ever lost any coins because of what remains a proof of concept.
Some Background
We initially designed Ledger hardware wallets because computers cannot be considered secure. A malware or virus could replace the receiving address on a computer with another one, tricking the user into sending funds to an unintended third-party (possibly the attacker).
Hardware wallets provide an isolation layer between the computer and the seed (your private keys). However, users must always ensure that they are sending coins to the correct address when transacting.
The Proof of Concept attack
Researchers published a proof of concept attack in which a malware modifies the Ledger Chrome application in order to edit the received address displayed on the computer screen.
As far as we know, this is only a proof of concept phishing attack and no Ledger user has ever been fooled using this technique. We were already aware of this scenario: computers cannot be considered secure, and therefore you cannot trust what you see on the screen. That’s the very reason why we decided to create the Ledger hardware wallet in the first place.
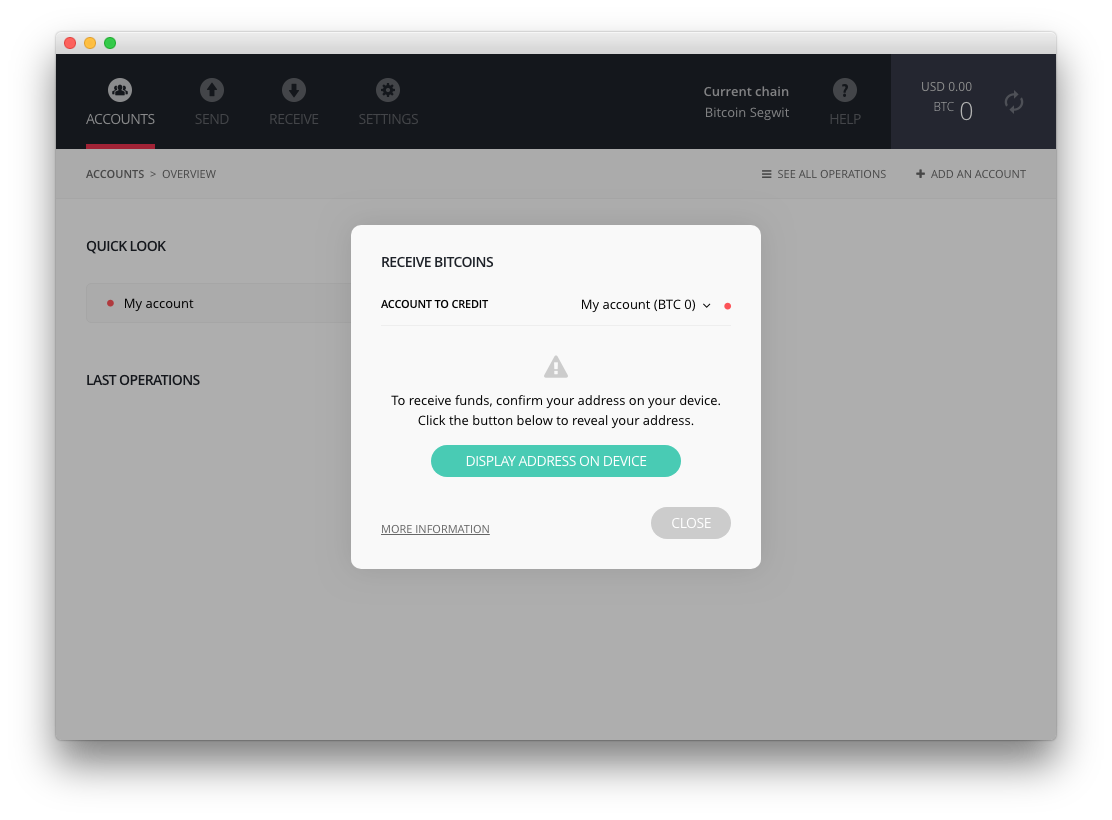
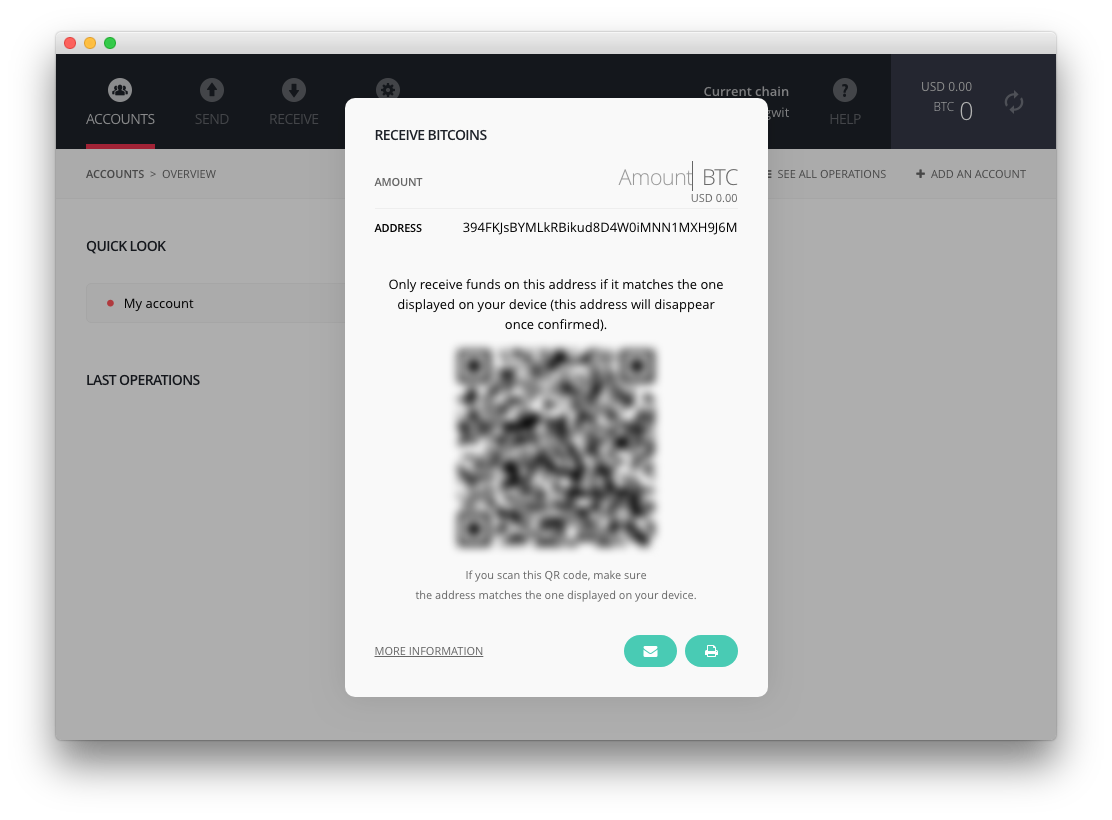
We would like to insist on the fact that in a threat model where the attacker is able to do anything on the computer, it is impossible to trust what is displayed on the computer screen. The only thing users can completely trust is what is displayed on the screen of their Ledger hardware wallet. The Ledger Wallet Bitcoin Chrome application also has a dedicated icon (third one from the left hand side, see image above) allowing the user to display the receiving address on their Ledger device. When the user clicks on this icon, the correct address is generated by the wallet and displayed on the Ledger hardware wallet’s screen. This is the only information you can trust.
Action Points
At Ledger, we strive to provide our users with an easy and secure way to manage their crypto assets. In order to avoid any misuse, we will keep providing our community with additional services and information, starting with the ones listed below.
- Software update: we released an update to the Ledger Wallet Bitcoin Chrome application that will request users to verify destination addresses on their Ledger hardware device – not just on the screen of their computer. Bitcoin & altcoins are getting the new feature (ETH and XRP apps will benefit from the feature in the new global release)
- Upgraded Bug Bounty program: we are growing quickly – and we are still developing and strengthening some of our behind the scenes processes. We value contributions from security researchers and the community, and will be making our Bug Bounty programs faster and more efficient. We already a dedicated mail address set up: [email protected]
- Education: security is an arms race – but we’re in it for the long haul. We plan to continue working on resources and materials to help educate our community on the threats they face and how they can best secure their assets. We invite you to read our basic security principles ruleset.
Make sure your apps on the Nano S are updated to the latest version (using the Ledger Manager). We will publish more information about the Ledger Wallet desktop application in the coming days.
Charles GUILLEMET
Chief Security Officer at Ledger
