Blog posts, Produto | 06/24/2025
A Technical Overview of Ledger Recovery Key
Ledger Recovery Key is the upcoming addition to our suite of recovery solutions. Understand its architectural design, security, and cryptographic protocols.
This blog post provides an overview of Ledger Recovery Key, including its architectural design, security, and the cryptographic protocols employed, summarising the more detailed technical White Paper*.
The technology described in this blog post is the subject of one or more pending patent applications. The publication of this blog post does not grant, either expressly or impliedly, any license, right, or permission to make, use, sell, or otherwise distribute the described technology.
Before you dive in
- Ledger Recovery Key is a PIN-protected backup card securely storing a copy of your 24-word Secret Recovery Phrase
- It features an embedded Secure Element chip powered by an operating system, the combination of which is certified from a security perspective
- Ledger Recovery Key communicates with NFC-supported Ledger devices
- Ledger Recovery Key is a complement to, not a replacement of, the traditional Recovery Sheet that remains the recommended form of backup
| Keyword | Meaning |
|---|---|
| HSM | Hardware Security Module |
| NFC | Near Field Communication |
| PIN | Personal Identification Number |
| SE | Secure Element |
Ledger Recovery Key – From a user perspective
Ledger Recovery Key is a physical backup card that can be used to store a copy of your master secret (which your Secret Recovery Phrase stems from) from your NFC-supported Ledger Hardware Wallet.
The Ledger Recovery Key product can only use the NFC protocol to communicate with a Ledger Hardware Wallet.
Ledger Recovery Key is not a Hardware Wallet, since it is not possible to use it to manage assets nor sign transactions.
Let’s take a look at the security design:
| Security | Comments |
|---|---|
| Security at rest | • The product has an embedded Secure Element chip powered by a certified operating system – the same type of hardware security Ledger uses within its Hardware Wallets. |
| Security at use | • The Ledger Recovery Key and Ledger Hardware Wallet perform a mutual authentication, allowing them to attest to the genuineness of their counterpart. • The product is PIN-protected, and three wrong PIN verification attempts will trigger the product to wipe its memory. • The communication protocol is secured and ensures confidential and authenticated data transfer. |
| Secure display | • The Ledger Recovery Key and Ledger Hardware Wallet perform a mutual authentication, allowing them to attest to the genuineness of their counterpart. • The product is PIN-protected, and three wrong PIN verification attempts will trigger the product to wipe its memory. • The communication protocol is secured and ensures confidential and authenticated data transfer. |
In the flow diagrams throughout this article, the different colors indicate:
- An onboarded device in green
- A non-onboarded device in blue
We can now look at the four main user features of Ledger Recovery Key:
- Backup
- Restoration
- Management
- Updates
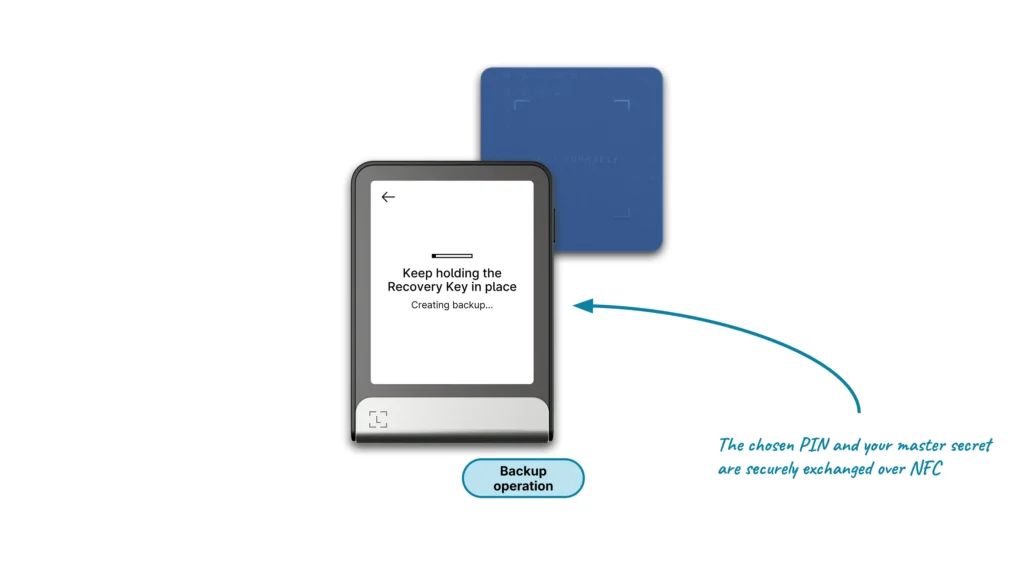
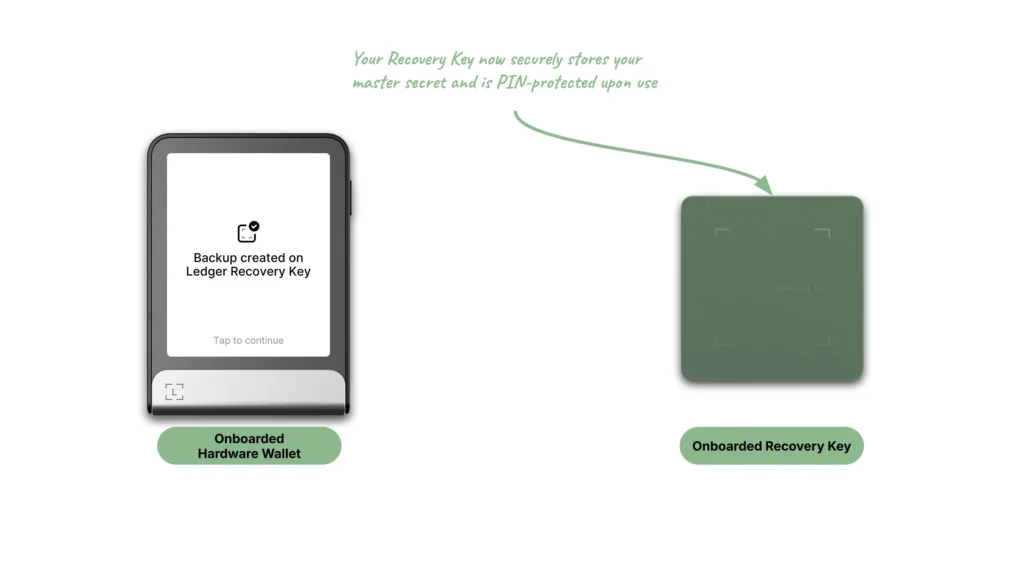
Backup to a Ledger Recovery Key
The first feature allows the user to make a backup of their master secret from their Ledger Hardware Wallet to their Ledger Recovery Key, and this will occur under one of two circumstances:
- At the end of the onboarding process, for a new Ledger Hardware Wallet,
- At any moment, for an already onboarded device.
The user shall:
- Follow the instructions prompted on the Ledger Hardware Wallet interface
- Create a PIN for the Ledger Recovery Key
- Tap it on the Ledger Hardware Wallet so that all the information can be securely transferred to the Ledger Recovery Key via NFC
The Ledger Hardware Wallet’s PIN is required to interact with the Ledger Recovery Key product.

Restore from a Ledger Recovery Key
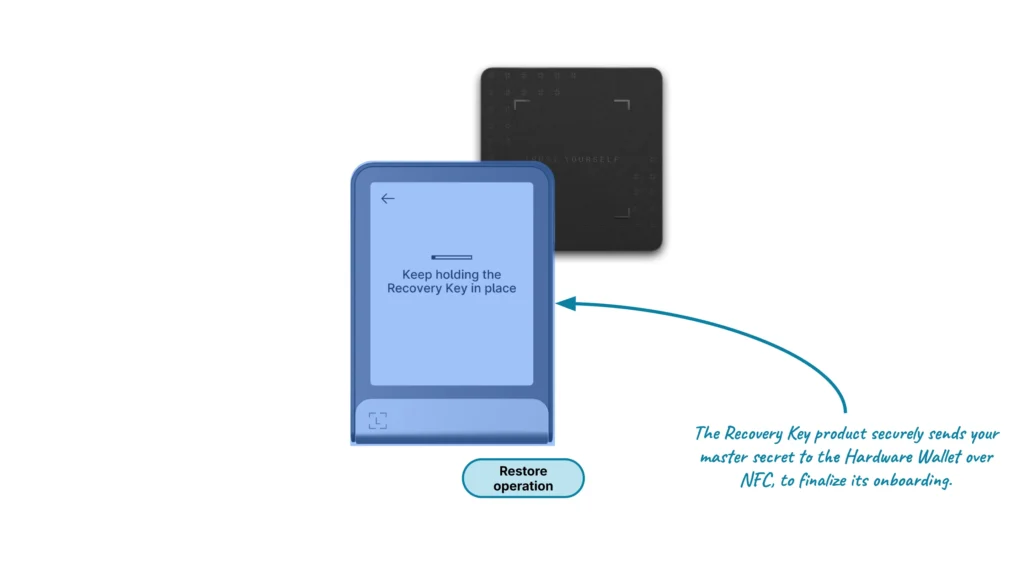
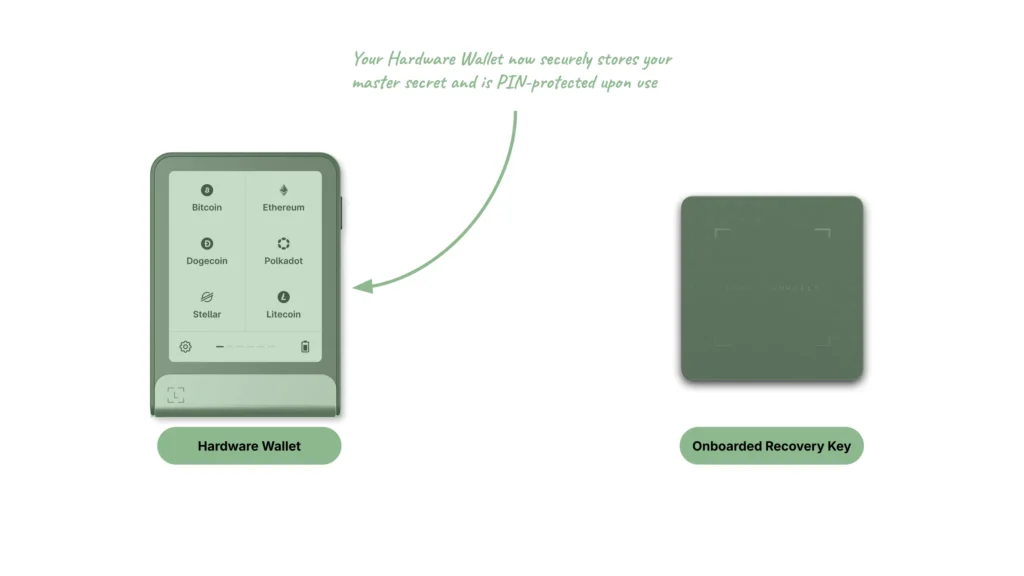
The second feature allows the user to copy their master secret from their Ledger Recovery Key to their Ledger Hardware Wallet. To use this feature, the Ledger Hardware Wallet must not be onboarded yet and thus, not yet contain a master secret.

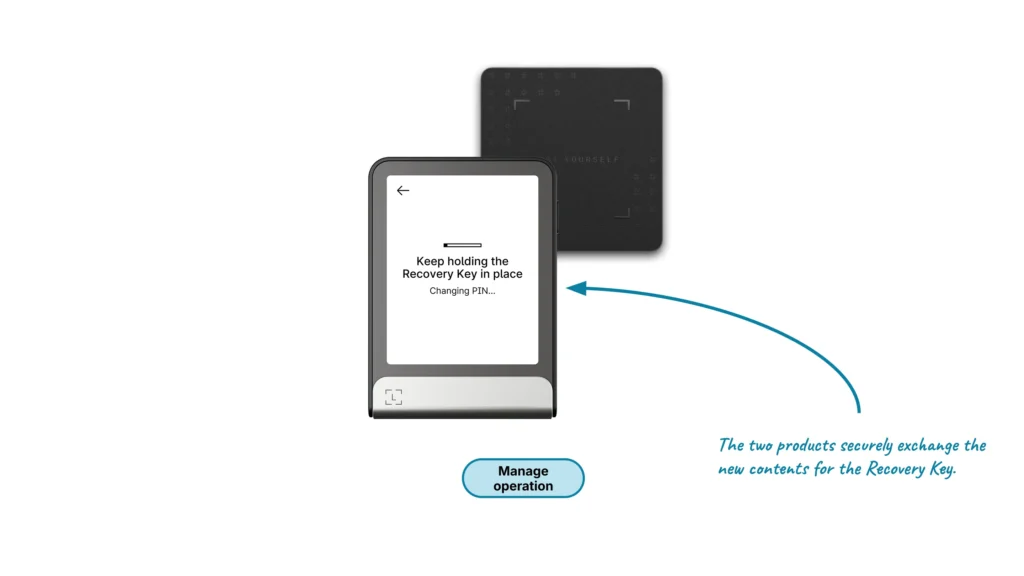
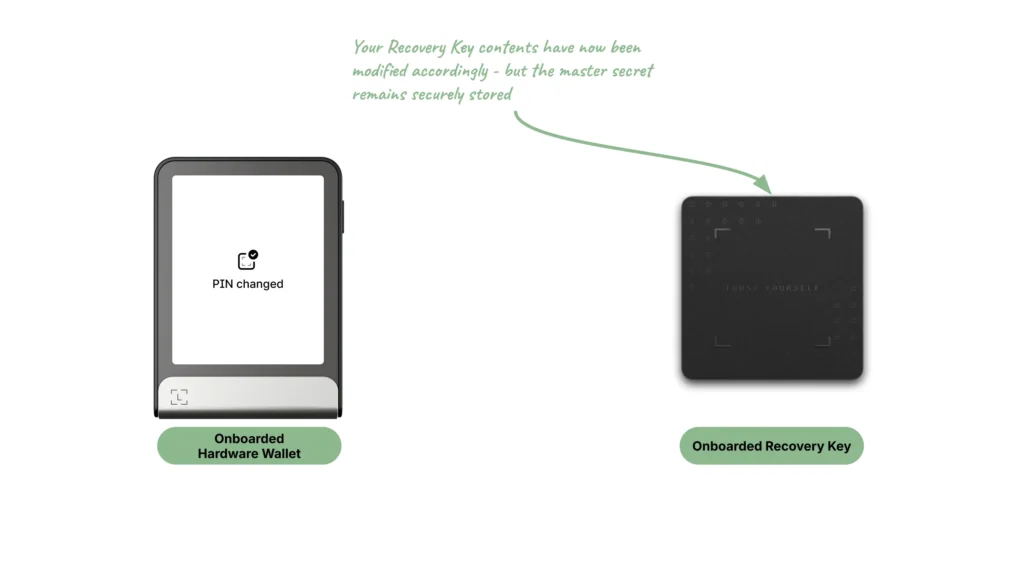
Manage Ledger Recovery Key contents
The third feature allows the user to manage their Ledger Recovery Key contents, such as:
- Changing its PIN
- Creating, changing, or deleting its name
- Wiping the user’s data (master secret, PIN, and name) to restore the product to its factory settings
The Ledger Hardware Wallet and the Ledger Recovery Key products must both be onboarded.

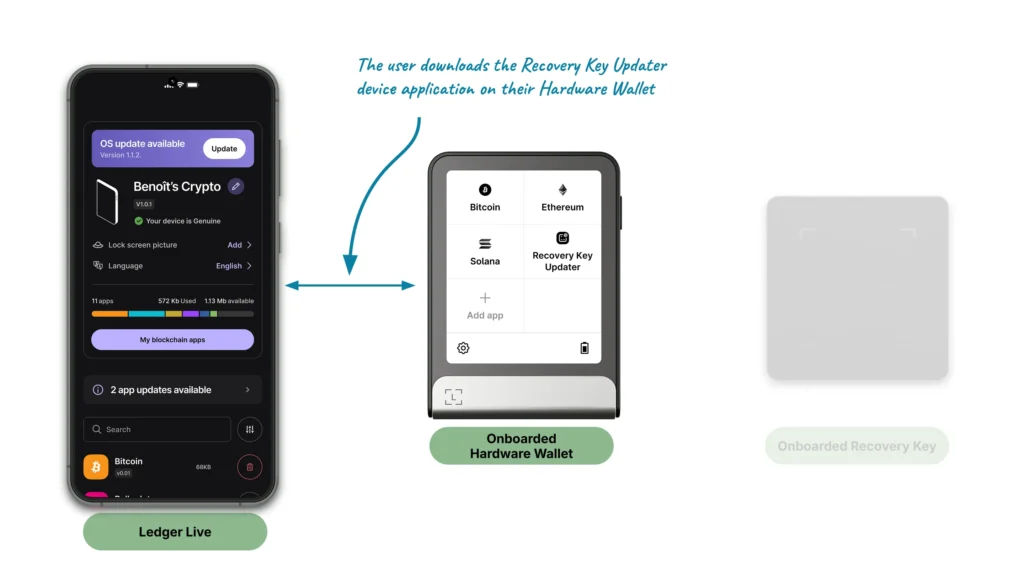
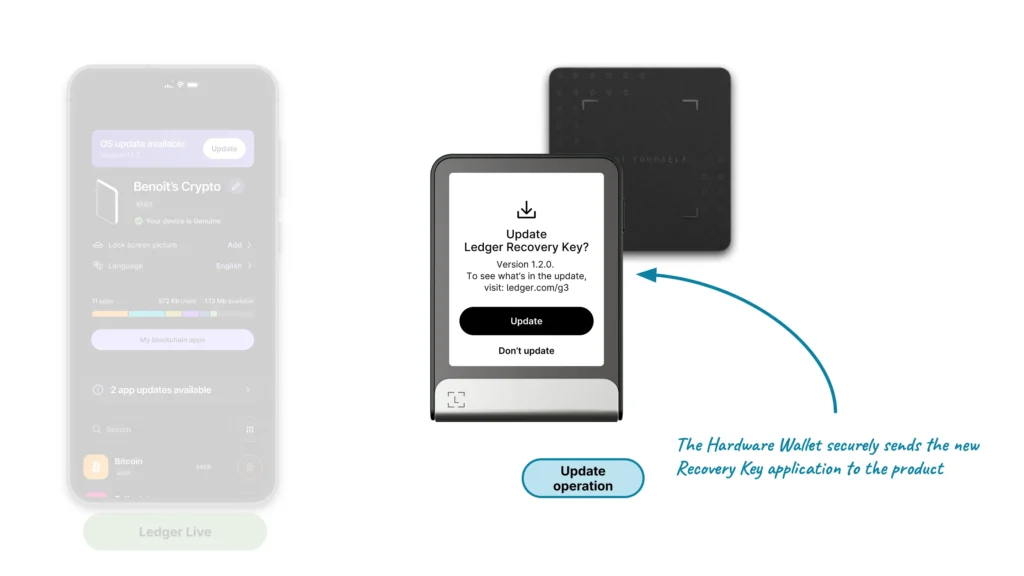
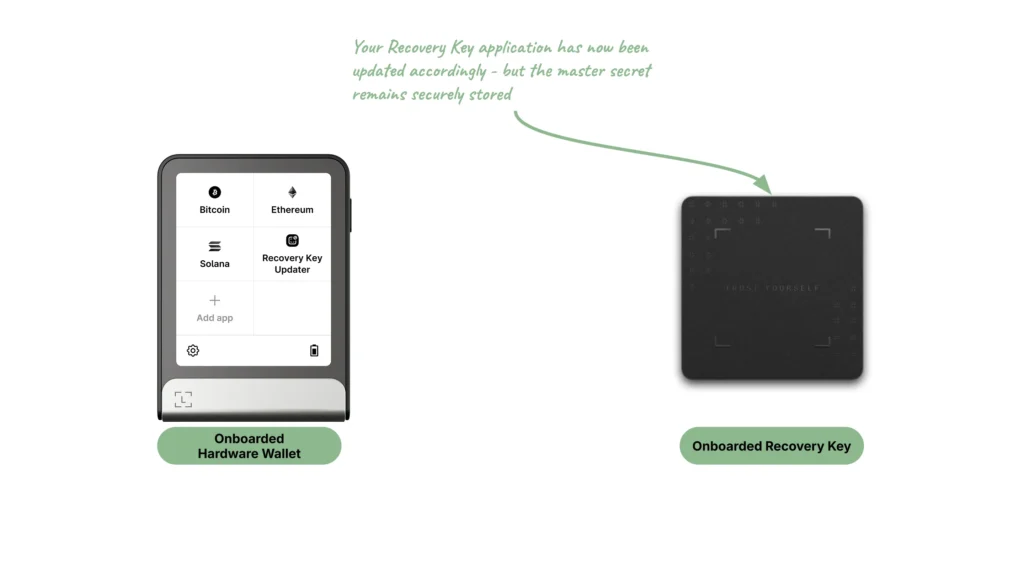
Ledger Recovery Key update
The fourth and last feature allows the user to update a portion of their Ledger Recovery Key software. This can happen for several reasons:
- Adding features
- Fixing issues
- Improving the security of the card over time
At Ledger, we consider that the security of our products cannot be static. We need to make sure we implement and deploy the necessary security improvements when needed. To this extent, the Ledger source code of the application running on the Ledger Recovery Key product is made available on GitHub to make sure our users can verify the implementation.
In the same vein that updating an onboarded Ledger Hardware Wallet is not possible without validating the user consent via verifying their PIN, updating an onboarded Ledger Recovery Key product can only be performed after having verified its own PIN, which is one of the reasons why updating the Ledger Recovery Key software can only be performed from a Ledger Hardware Wallet.
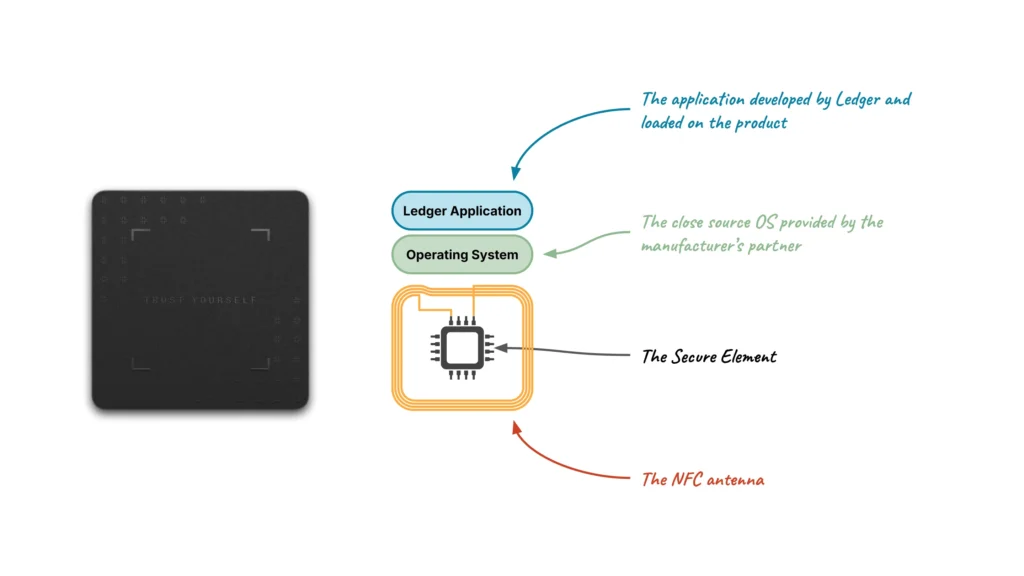
Secure elements & HSMs
As mentioned in the Ledger Recover white paper, a Secure Element is a tamper-resistant processor chip, providing security countermeasures aiming to resist a wide range of attacks.
Operating Systems powering these Secure Elements usually leverage these security features to protect secret data, to isolate the execution of the different components from each other, and to resist attacks aiming to extract this secret data. The embedded software stack powering Ledger Hardware Wallets is designed to provide several security mechanisms to this extent, as mentioned in our Donjon threat model.
An HSM is a physical device, most commonly found under the form factor of a network interface controller, used to manage and securely store secret data, usually cryptographic keys, and which provides an interface dedicated to performing cryptographic computations with these keys from within the secure environment.
Typical use cases range from managing keys for website security to payment transaction processing, banking cards production, and much more. In the sense of the security guarantees these two types of hardware components provide, one could consider a Secure Element as a portable HSM.
Ledger Recovery Key – From a design perspective
Ledger developed a Java Card application responsible for executing the business logic and combining secure data transfers with secure storage and cryptographic computations. The source code is verifiable on our GitHub repository allowing everyone to check the Ledger implementation on the Ledger Recovery Key product which can be found here:
Within the Ledger Recovery Key product, the Secure Element is an NXP P71D600 provided with a JCOP4.5 operating system. The combination of these two items has passed a Common Criteria EAL6+ security certification:
- Common Criteria Security Target Light
- Common Criteria Certification Report
The secure storage in the Ledger Recovery Key product thus relies on both the Secure Element and associated operating system embedded in the product, but also on the Ledger application managing the PIN and the cryptographic keys.
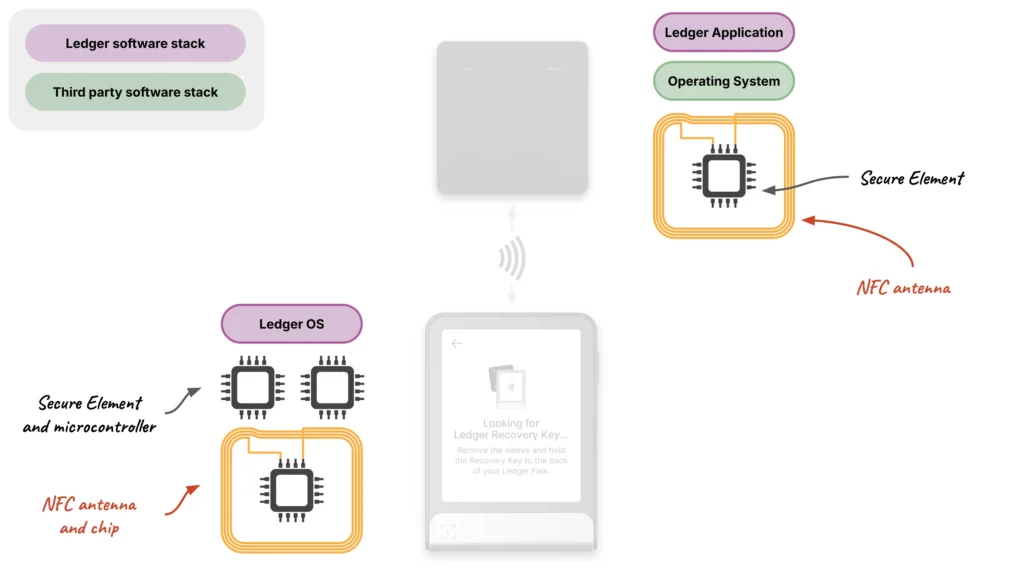
Ledger Recovery Key – From a component perspective
We can now look at the interactions of the Ledger Recovery Key product with the other main technical Ledger components:
- The HSM, involved in the Ledger Recovery Key manufacturing and updates preparation
- The Ledger Hardware Wallet with NFC capabilities
- The Ledger Recovery Key product itself
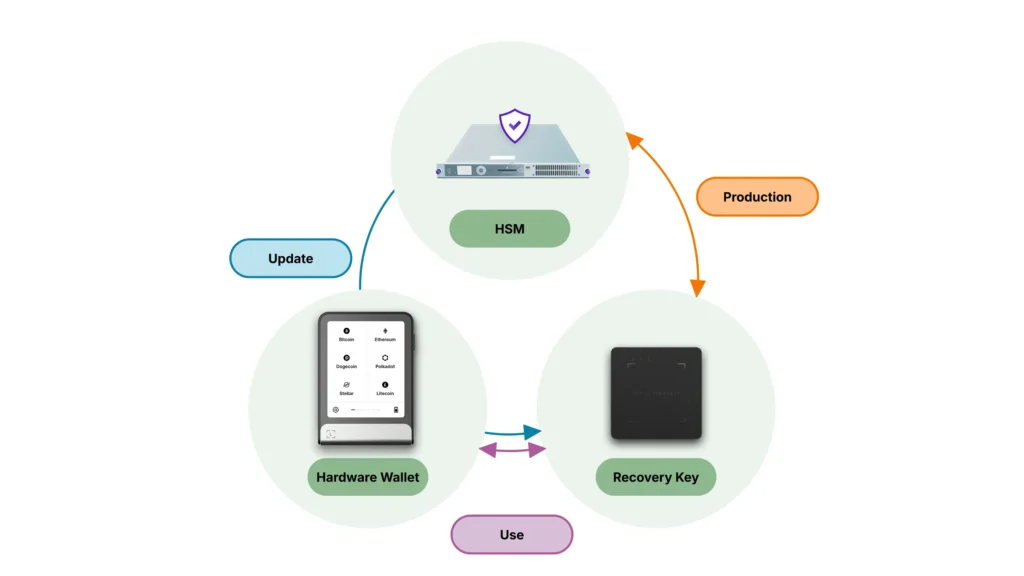
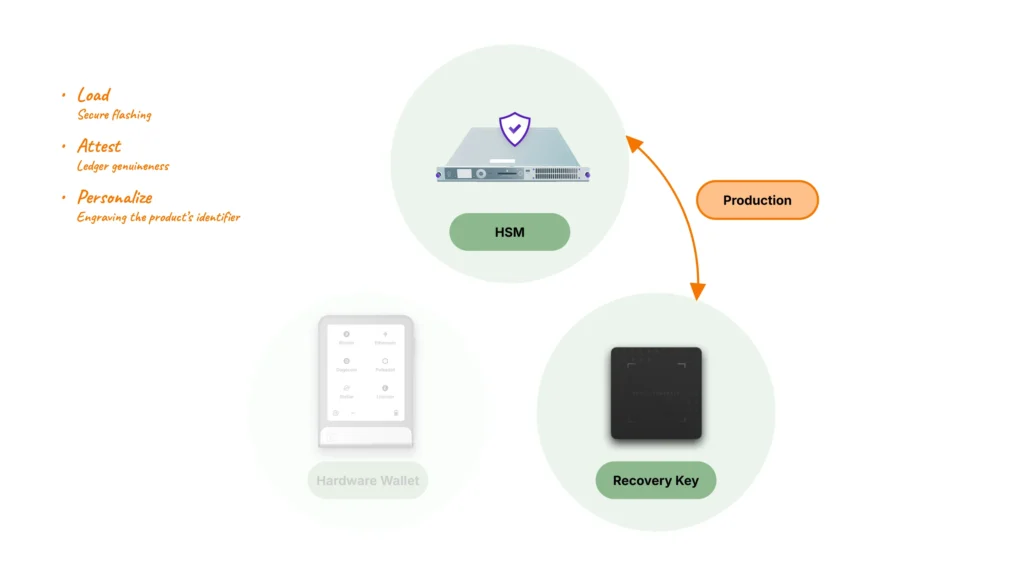
Factory
The Ledger Recovery Key factory production environment is controlled in Ledger facilities, at Vierzon. This geographical positioning, along with initial sets of cryptography keys, allows Ledger to make sure the produced Ledger Recovery Key products are originating from Ledger. The environment is twofold:
- The manufacturing process – the Operating System is provided with specific cryptographic keys, ensuring that applications can only be loaded if signed by Ledger HSMs
- The functional preparation – the application is loaded on top of the OS, and cryptographic operations are conducted between Ledger Recovery Key and our HSMs to create and securely store the unique attestation data, aiming at making the Ledger Recovery Key product successfully pass the genuine check once in the field
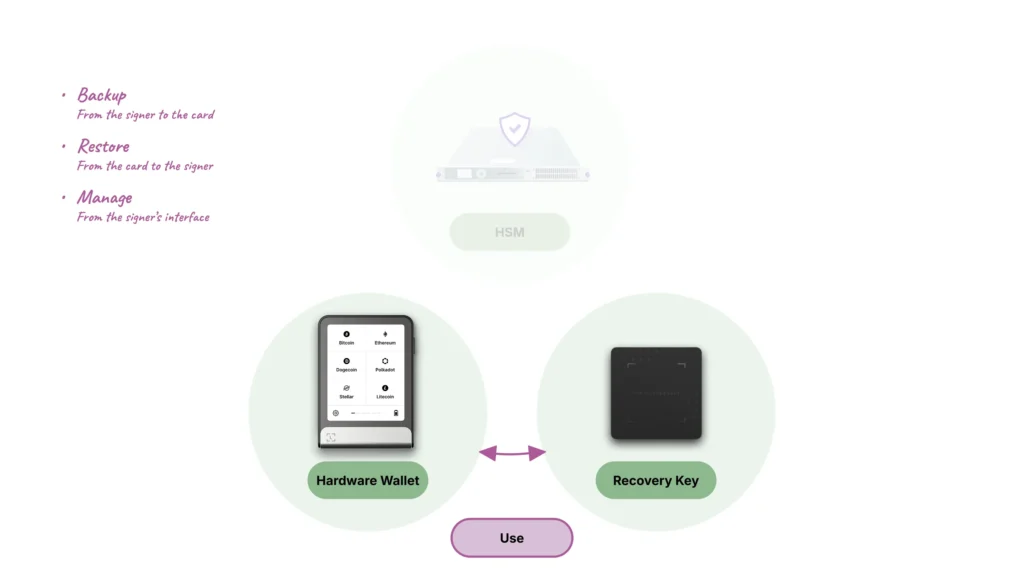
Usage in the field
As presented in previous paragraphs, using the Ledger Recovery Key product is performed locally between the Ledger Hardware Wallet and the product, via NFC.
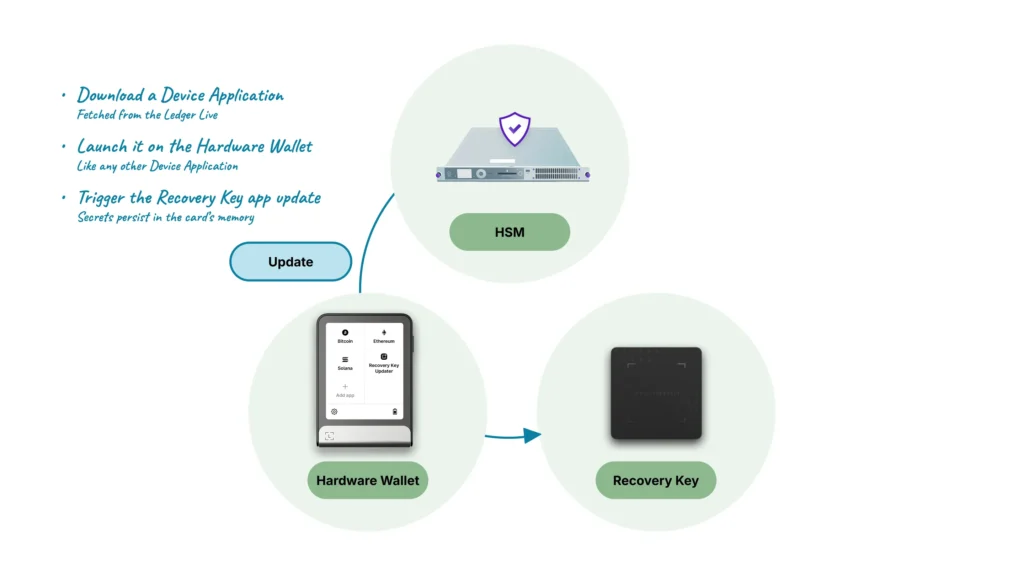
Updating in the field
Updating the Ledger Recovery Key to benefit from an improved application on the product itself is performed in several steps:
- Downloading a specific application on the Ledger Hardware Wallet, containing the Ledger Recovery Key update
- Launching it on the Ledger Hardware Wallet
- Following the associated steps and waiting for the update to be fully transferred onto the Ledger Recovery Key
Secure operations
The cryptography algorithms used within the overall communication protocols are the following.
| Encryption | MAC | Hash | Signature Verification | Key Exchange | KDF | |
|---|---|---|---|---|---|---|
| SCP03 | AES-CBC | CMAC-AES | – | – | – | CMAC-AES |
| Genuine check | – | – | SHA256 | ECDSASECP256K1 | ECDHSECP256K1 | SHA256 |
| PIN | AES-CBC | HMACSHA512 | SHA256 | – | – | – |
| Seed transfer | AES-CBC | HMACSHA512 | – | – | – | – |
To go further regarding these algorithms, please find related standards and pieces of information in the following table.
| Keyword | Meaning |
|---|---|
| AES-CBC | AES symmetric encryption algorithm used in CBC mode |
| AES-CMAC | AES-CMAC algorithm |
| ECDH | Elliptic Curve Diffie-Hellman |
| ECDSA | Elliptic Curve Digital Signature Algorithm |
| HMAC | Keyed-Hash Message Authentication Code |
| SCP03 | Secure Channel Protocol ‘03’ |
| SECP256K1 | Recommended Elliptic Curves Domain Parameters |
| SHA256 / SHA512 | Secure Hash Standard |
Secure channel – SCP03
The first layer of security protocol set up between the Ledger Hardware Wallet and the Ledger Recovery Key product is a standardized Secure Channel – SCP03. The two products can create such a Secure Channel thanks to the AES keys they already contain and the manufacturing process.
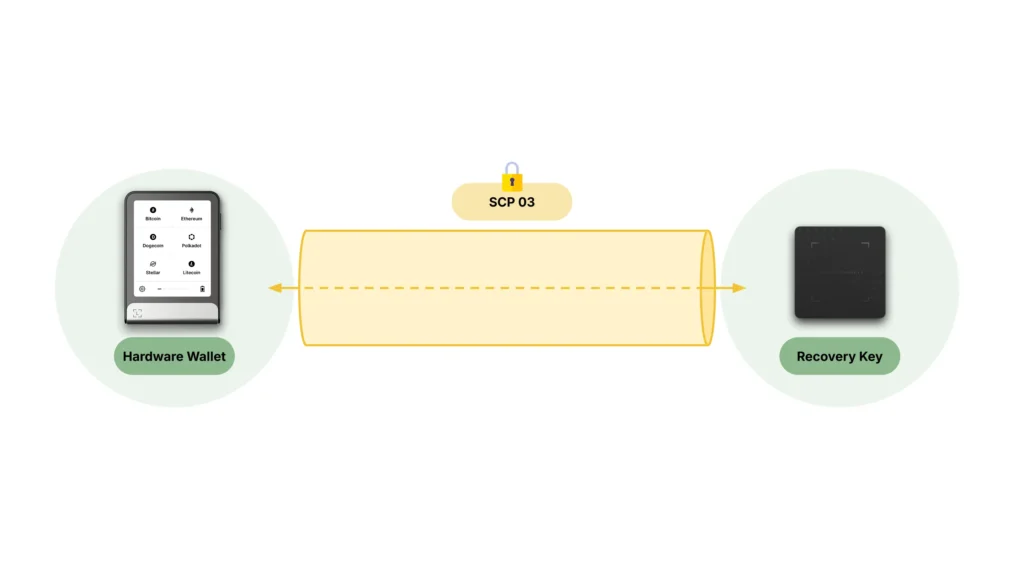
Secure channel – Ledger
Once the SCP03 secure channel has been created between the two products, they exchange information (securely within this Secure Channel) to create another Secure Channel, which Ledger is already using between its Hardware Wallets and its HSMs.
This Ledger-based protocol is also used by the two products to mutually check their respective software genuineness by cross-checking their cryptographic attestation.
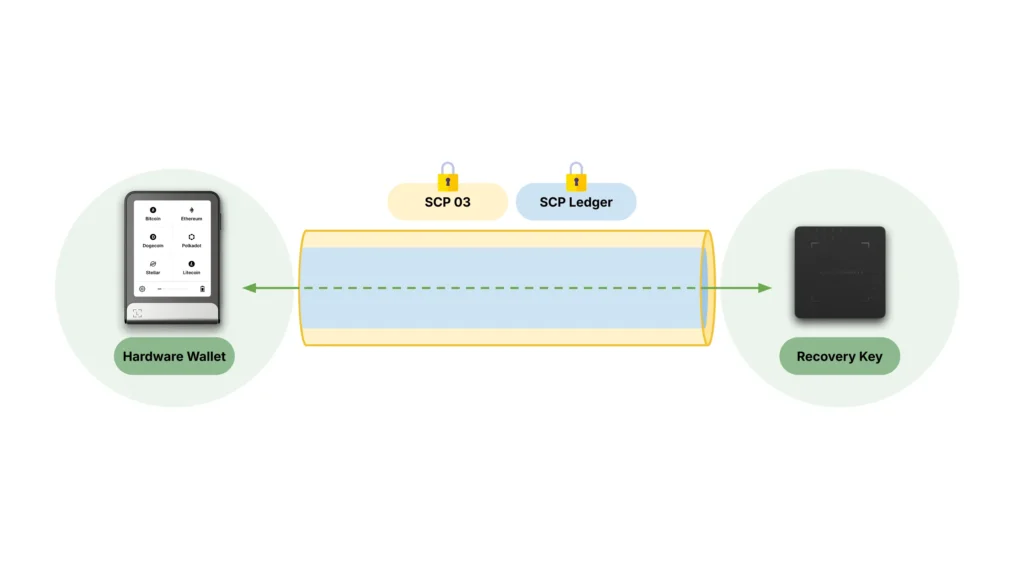
Secured operations
All the Ledger Recovery Key features are conducted within the combination of these two Secure Channels, by exchanging data between the two products as represented by the green arrow on the picture above:
- Creating the Ledger Recovery Key PIN
- Storing the user’s secret data in the Ledger Recovery Key
- Verifying the PIN to unlock the Ledger Recovery Key
- Restoring the master secret from the Ledger Recovery Key to the Ledger Hardware Wallet
- Changing the Ledger Recovery Key’s PIN
- Creating, changing, or deleting the Ledger Recovery Key’s name
- Wiping the Ledger Recovery Key
Conclusion
In conclusion, and as shown in this document from a high-level perspective, Ledger makes use of state-of-the-art and certified secure storage coupled with secure cryptographic protocols to ensure the Ledger Recovery Key product gets provided with end-to-end security, in particular when it comes to:
- Manufacturing and attesting it with our HSMs
- Using it in the field, on both the security at rest and security at use aspects
- Updating it in the field if needed
Authored by Raphaël Geslain (Embedded Software Director)
References:
*Ledger Recovery Key White Paper – A detailed description of Ledger Recovery Key’s architectural design, security, and cryptographic protocols.































